The Citrix Software Defined Perimeter model means treating the user to the centre of your security world: The user is the new edge of your environment.
This makes sense as the workspace has morphed from a well-defined entity contained in your data centre, to a new and challenging landscape encompassing corporate controlled apps and data, cloud solutions and SaaS (Software as a Service) applications. The common factor in accessing all of these is the user, so how exactly do you secure a user?
Putting the user in the middle
Citrix offer a highly capable workspace solution which provides the ability to deliver corporate apps and data from on-premises and the cloud, alongside integrated SaaS applications. This covers the access and user experience aspects; however, it doesn’t directly address securing the user.
The new Citrix Analytics service provides user behaviour analytics to determine a risk profile for a user, based on their activities in your environment. This allows for not only identification of potential risks from within your environment, but also the ability to implement rule-based remediation. For example, if a user is identified as copying documents to local removable storage, you can define actions such as forcing the user to log off or starting Session Recording to capture what they are doing for an administrator to review.
The ability to monitor and respond to user behaviour in Citrix Workspace is a powerful new capability, but its focus is on monitoring and responding to activities in your environment that could indicate that a user account has been compromised, or even an internal bad-actor. But what is the precursor to this?
User Identity provides the keys to access your corporate resources. With a valid user identity your perimeter defences can be compromised, allowing external threats access to your environment. In the current threat climate user identities are invaluable to attackers allowing a foothold which, for even unprivileged accounts, can be leveraged to move sideways in your network and gain access to sensitive systems and data.
How do we protect the user identity?
Microsoft offer a feature of Azure Active Directory (AAD) called Azure Identity Protection (AIP). AIP protects user identities for your users by implementing a variety of protective measures including using heuristics and machine learning to identify;
- Users with leaked credentials
- Impossible travel to atypical locations
- Sign-ins from anonymous IP addresses, IP addresses with suspicious activity, unfamiliar locations and infected devices
These detections leverage the Microsoft Security Graph which is comprised of data from a worldwide set of detectors and data sets collected from the entire Microsoft online portfolio.
The result is that each time a user authenticates to AAD, AIP will determine the risk score for the authentication. Much like with Citrix Analytics we can not only monitor, but respond to these risk events – in the case of AIP by levelling-up the authentication requirements (by requiring Multi-Factor Authentication) or blocking the authentication based on the risk level.
How is this used with Citrix Workspaces?
Using FAS, or Citrix Federated Authentication Service, we have the ability to use SAML authentication from external identity providers such as Azure AD to authenticate to Windows Sessions using virtual Smart Cards as shown in the diagram below:
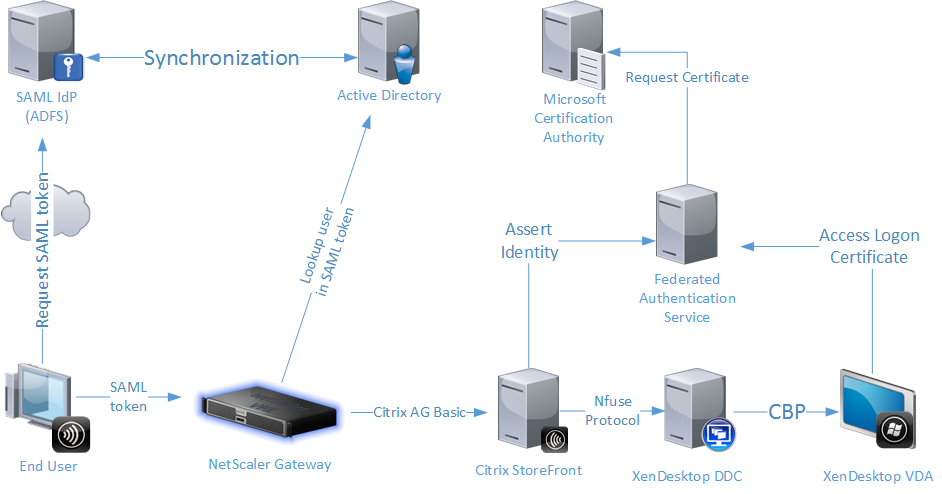
Typically you would expect to see SAML authentication being used for 3rd party users, or for accessing external systems. It is possible however, to implement Azure AD to utilise Azure AD Connect using seamless SSO, which then enables internal users to use Kerberos authentication to seamlessly authenticate to Azure AD and pass the Azure AD SAML token to StoreFront to authenticate.
Using seamless SSO is opportunistic, meaning that if a user who is configured for SSO is off-network and unable to use Kerberos authentication, then the authentication process will fall-back to browser-based sign-on using username and password.
To successfully deploy this solution, you will need:
- XenApp/XenDesktop 7.9 or higher
- StoreFront 3.9 or higher
- Azure Active Directory Premium P2
- Azure AD Connect
Through leveraging FAS in our deployment we can add the capabilities of Microsoft Azure Identity Protection to our Citrix Workspace solution, combining the best of Citrix and Microsoft to deliver Secure Digital Workspaces. To find out more about our solution, please get in touch with us.
- By Andrew McCullough (Solutions Architect)



