Growing connectivity along with evolving networks and technologies provide great opportunities for businesses, but also present new and more sophisticated threats. We are now facing Gen V (5th Generation) of cyberattacks, which are more sophisticated than ever, crossing mobile, cloud and networks, and bypassing conventional defenses that are based on detection.
The threat
The proliferation of smart mobile devices, virtual instances, public cloud, private cloud and Internet of Things (IOT) has disrupted IT security. Businesses need to digitally transform the way in which they operate in order to overcome these challenges.
Separate IT environments often drive businesses to apply multiple, disparate solutions, many of which focus on detection and mitigation rather than prevention. This reactive, unintegrated approach is costly and ineffective, complicates security operations and creates inherent gaps in security posture.
Enterprises need a more complete architecture that scales with dynamic business demands and focuses on prevention to ensure all IT environments are completely protected.
The solution
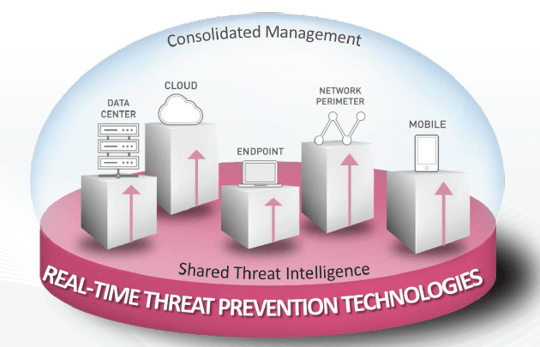
Check Point Infinity is the only fully-consolidated cyber security architecture that protects your business and IT infrastructure against Gen V cyberattacks across all networks, endpoint, cloud and mobile.
Infinity achieves this through three key elements:
1. One security platform- the architecture is designed to resolve the complexities of growing connectivity, providing the highest level of security on all platforms regardless of network or size. Check Point Infinity spans all of your IT assets – perimeter, data center, virtual, cloud, mobile and beyond, providing a wall of coordinated protection from advanced threats.
2. Preemptive threat prevention- to ensure business continuity, you need threat prevention that works non-stop, and can stop attacks before they infiltrate your network. heck Point Infinity enables you to stay ahead of attackers with real time threat prevention. Leveraging Check Point SandBlast technologies, it provides the most advanced threat prevention and zero-day protection blocking both known and unknown threats.
3. Consolidated system- Check Point Infinity is an architecture that gives you complete, unified control over the security across your networks, cloud and mobile from a single pane of glass. By providing security teams with a unified view, the team only have to learn and manage one security architecture, thereby increasing operational efficiencies, freeing up security teams to focus on strategic security rather than repetitive tasks. This consolidation also means a unified policy for users, data, applications and networks that introduces unparalleled granular control and consistent security.
Summary of key benefits
- Prevention-driven cyber security, powered by the most advanced threat prevention solutions against known and unknown threats
- Consistent security across all Check Point components with shared threat intelligence across networks, cloud and mobile
- Unified and efficient management of the entire security network through a single pane of glass
- Rich integrations with 3rd party solutions with flexible APIs
Read our data sheet on the link below to find out more.


